Technology is advancing at an exponential rate, but the advancements haven’t always brought the good with them. Sometimes, technology and advances can have unintended consequences that don’t have the intended goals and are more harmful than beneficial.
While ransomware poses a serious threat to users’ data, there are ways to protect yourself from it. In this article, we’ll discuss some of the ways you can protect your computer from ransomware in 2022.
What is ransomware?
Ransomware attacks are typically launched through email messages that contain infected attachments or links.
Ransomware is a type of malware that locks your computer screen and demands payment from you to release it.
Ransomware, also known as crypto-jacking, is a type of malware that encrypts data on a user’s computer until a ransom is paid to obtain the key to decrypt the files. This type of malware has become increasingly popular in recent years, with cybercriminals using it to extort money from victims.
How could ransomware affect my PC?
Ransomware could potentially lock your computer screen, prevent you from opening files, or encrypt your data. If you don’t pay the ransom, the perpetrator may delete your files or sell them to someone else.
Types of ransomware
There are two main types of ransomware: file-encrypting ransomware and crypto viral ransomware.
- File-encrypting ransomware locks files on your computer and demands payment to release them.
- Crypto viral ransomware encrypts entire hard drives and displays a ransom message demanding payment to unlock them.
There is no one type of ransomware that is more dangerous than the other; they all have unique features that can make them more difficult to remove.
It’s important to remember that no matter what type of ransomware your computer is infected with, there is always a chance that you may not be able to recover your files. However, using proper safety precautions can help protect your computer from being infected in the first place. Here are some tips for avoiding ransomware infections:
How does ransomware work?
Ransomware is a type of malware that encrypts a user’s files and demands ransom payments to release them. Once the files are encrypted, the ransomware can’t be opened or used.
To encrypt a file, ransomware first needs to access it. This can be done through a vulnerability in the user’s computer or by stealing the user’s login information. Once access is granted, the ransomware will encrypt the file using an encryption algorithm.
Ransomware often uses strong cryptography to protect its encryption keys. It’s also difficult for users to decrypt their files without knowing the encryption key. Therefore, victims are usually asked to pay a ransom to decrypt their files.
Ransomware can affect any type of computer, whether it’s a desktop or a laptop. It’s even possible for ransomware to infect smartphones and tablets.
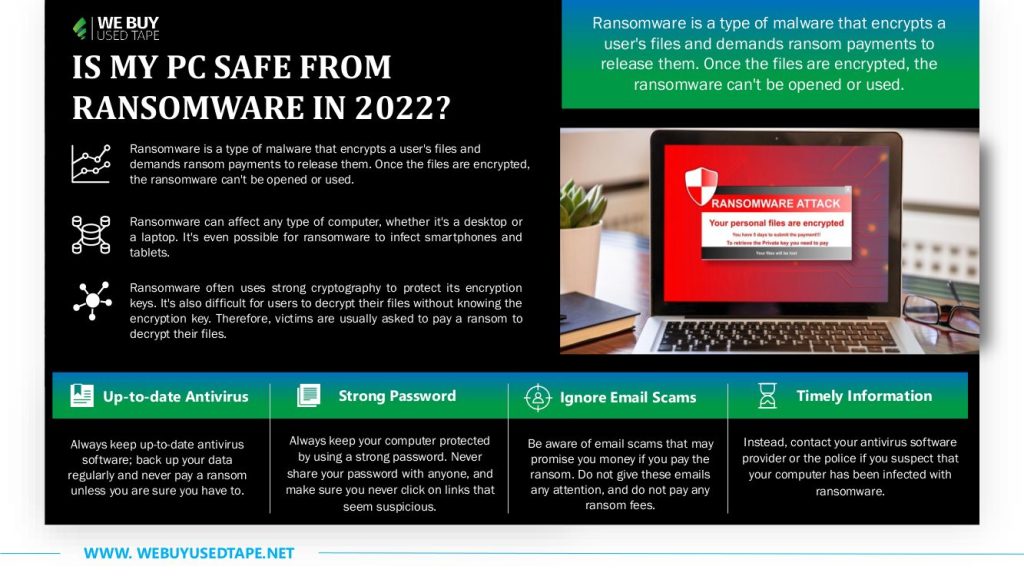
How to protect your computer from ransomware in 2022?
There are a few things you can do to protect yourself from ransomware: always keep up-to-date antivirus software; back up your data regularly and never pay a ransom unless you are sure you have to.
Ransomware is a type of malware that locks your computer and demands money from you to release it. It is one of the most common types of malware, and it is growing more and more popular each year.
There are a few things you can do to protect your computer from ransomware in 2022. First, make sure you have up-to-date anti-virus software installed on your computer. This will help to protect your computer from malicious files and viruses.
Second, make sure you always keep your computer protected by using a strong password. Never share your password with anyone, and make sure you never click on links that seem suspicious.
Finally, be aware of email scams that may promise you money if you pay the ransom. Do not give these emails any attention, and do not pay any ransom fees. Instead, contact your antivirus software provider or the police if you suspect that your computer has been infected with ransomware.
What are the symptoms of ransomware infection?
If you’re infected with ransomware, you may experience symptoms such as a slowdown in your computer’s performance, system errors, and unexpected pop-ups on your screen.
Ransomware is a type of malware that encrypts your files and demands payment from you to release them back to you. This means that you may not be able to access or use your files until you pay the ransom.
What to do if you’re infected with ransomware?
If you’re infected with ransomware, the first step is to remove the ransomware from your computer. This will help to protect your data and ensure that you can recover your files if necessary.
There are a variety of ways to remove ransomware. You can use malware removal tools, such as those offered by Microsoft or Malwarebytes. You can also try to remove the ransomware using manual methods, such as deleting the files associated with it. If you’re unable to remove the ransomware using any of these methods, you may need to contact a cybersecurity services provider for assistance.
Ransomware targeting PCs in 2022
In 2022, ransomware will be a major concern for businesses and individuals. The types of ransomware that will be targeting PCs in 2022 include banking Trojans, email viruses, and ransomware variants targeting the healthcare industry.
The biggest threat posed by ransomware is not just to businesses, but also to individuals who use their PCs for personal activities. If you are a business owner or individual who relies on your computer for work or personal use, it is important to take steps to protect yourself from ransomware infection.
Why would someone ask for money in the form of crypto to unlock their PC?
There are a few reasons why someone might ask for money in the form of crypto to unlock their PC.
One reason is that ransomware can encrypt the files on a computer, making them inaccessible until the user pays the ransom. The crypto used in this type of ransomware is often called Bitcoin because it is stored in BTC (Bitcoin) addresses.
Crypto-ransomware also creates ads that try to trick users into installing an infected program. These ads appear to be from reputable websites or legitimate software manufacturers and promise to help you fix problems with your computer. However, when you install the program, it installs ransomware on your system.
Many people who pay crypto-ransomware demands don’t realize it until it’s too late and their computer is locked down. In many cases, the only way to unlock the computer is to pay the ransom. If you’re worried that your PC may be infected with crypto-ransomware, you can use a security solution to scan for infections and remove any possible threats.
Conclusion
Ransomware is a big problem and it’s only going to get worse. So, what can you do to protect your PC from this type of attack? Here are a few tips:
- Back up your data regularly – even if you don’t think you need to because your files are backed up on your computer automatically. This way, in the event, that ransomware makes off with your data, at least you won’t lose everything irreplaceable.
- Use strong passwords – not just the usual easy-to-remember ones, but memorable combinations of letters and numbers as well. Make sure to change them regularly so that even if someone gets access to your password file they won’t be able to use it to access all of your other important accounts online.
- Install antivirus software and keep it up-to-date – even if you think you don’t need it because you trust the security features of your PC manufacturer
